Penetration Testing
Our pentesting service is the essential tool to prevent cyberattacks before they happen. Through an active, strategic security audit, we simulate real-world attacks to uncover critical vulnerabilities in your systems. This allows you to stay one step ahead of threats, strengthen your defenses, and ensure uninterrupted operations—no surprises.

What is a Pentesting service?
Pentesting, or penetration testing, involves assessing the security of a digital infrastructure by attempting to exploit it—just as a cybercriminal would, but in a controlled environment. This process includes:
-
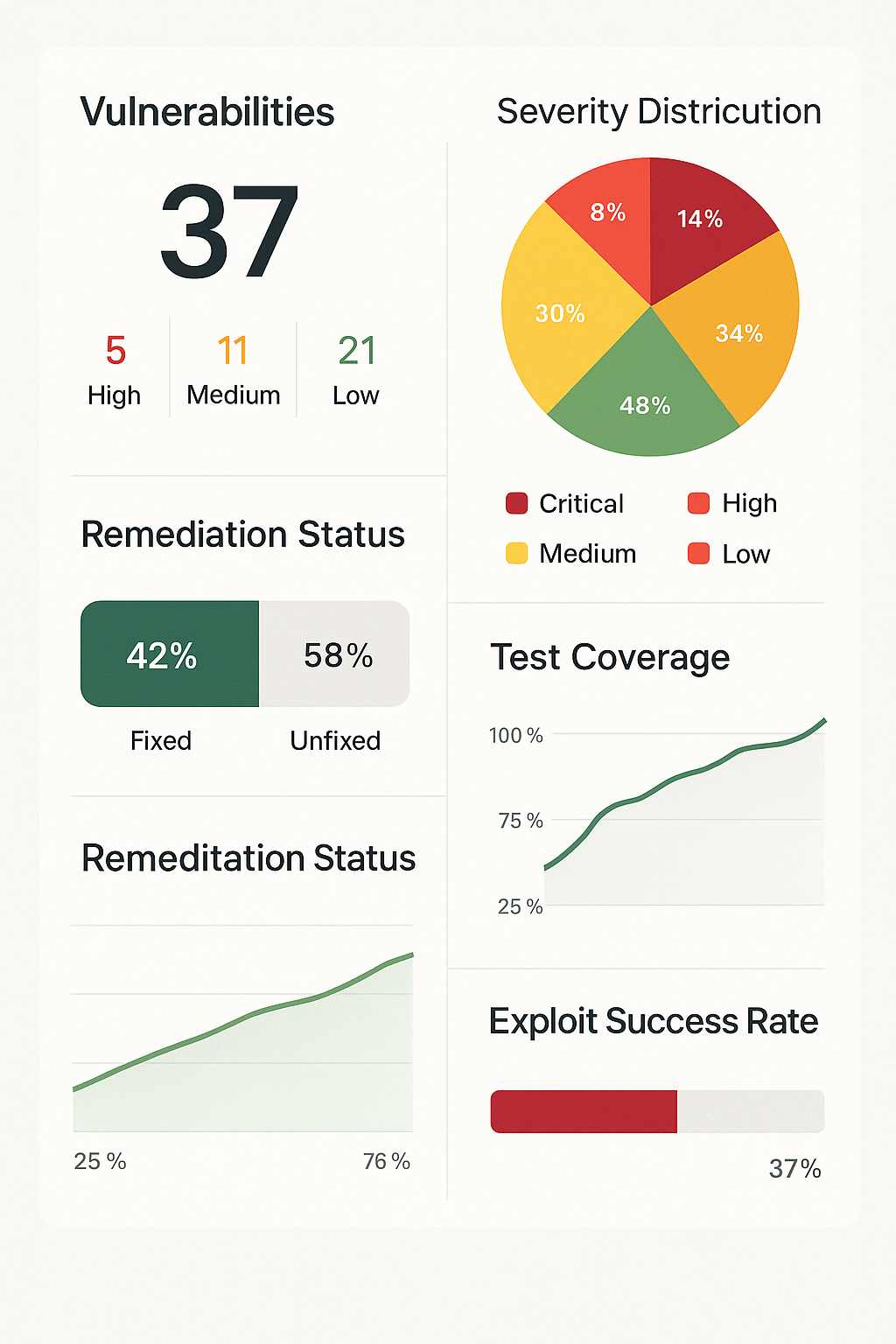
Vulnerability Identification in networks, applications, and systems
-
Controlled Exploitation of weaknesses to measure their real-world impact
-
Comprehensive Technical Report detailing findings and recommendations
Unlike automated scans, our pentesting service blends advanced tooling with expert analysis to deliver complete, precise coverage.
Benefits of a Security Audit
Vulnerability Identification
We pinpoint weak spots before attackers do.
Reduced Exposure Time
By understanding your risks, you can deploy patches and controls immediately.
Proactive Remediation & Mitigation
We prioritize flaws by real risk level and cost to exploit.
Advanced Threat Protection
We simulate sophisticated attacks—from standard breaches to zero-day exploits.
Why Your Company Needs Penetration Testing
Proactive Risk Detection
Without realistic testing, many flaws remain unnoticed until they’re exploited.
Critical Asset Protection
Sensitive data, intellectual property, and brand reputation hinge on your security posture.
Increased Confidence
Clients and partners value companies that employ cutting-edge enterprise cybersecurity.
Regulatory Compliance
Standards like ISO 27001, GDPR, and NIS2 require regular audits and penetration tests.
Resource Optimization
Investing in offensive security consulting prevents costly incidents and reduces total cost of ownership (TCO).
Post-Pentesting Support
After delivering the report, we guide your team through remediation and validate that implemented measures truly close the gaps discovered.
Technical Guidance & Validation
We plan and prioritize patches by risk, then perform targeted re-testing to confirm vulnerabilities are resolved.
Executive Closure Report
A concise summary for leadership, outlining improvements made, key metrics, and the level of resilience achieved.
Our Pentesting Approaches:
Black Box & White Box
Black Box Pentesting
Audit without prior information of the infrastructure, with a realistic approach.
Simulates the point of view of an external attacker, identifying possible vectors.
Ideal for measuring resistance to unknown intruders, evaluating critical breaches.
Pentesting White Box
Audit with access and documentation of the system, focusing on proactive threat analysis.
Allows in-depth review of code, configurations and internal processes.
Perfect for in-depth audits and detection of complex vulnerabilities.
