Zero-Day Attack: What is it and How to Prevent It?
Zero-day attacks take advantage of software flaws that are unknown to the software’s developers to target victims without prior warning. These attacks grow more common every year, so it’s important to know the risks.
What is a zero-day attack?
Hackers are facilitated in their ability to attack and infiltrate a company’s systems by potential vulnerabilities in software, both in the operating system and in other software used. If they find a particular vulnerability, they can exploit it to carry out all kinds of attacks against the system.
A zero-day attack means that the company is under attack because of a flaw in its systems and that, if it does not react quickly and appropriately, the consequences can be very negative, both from an operational, financial and reputational point of view.
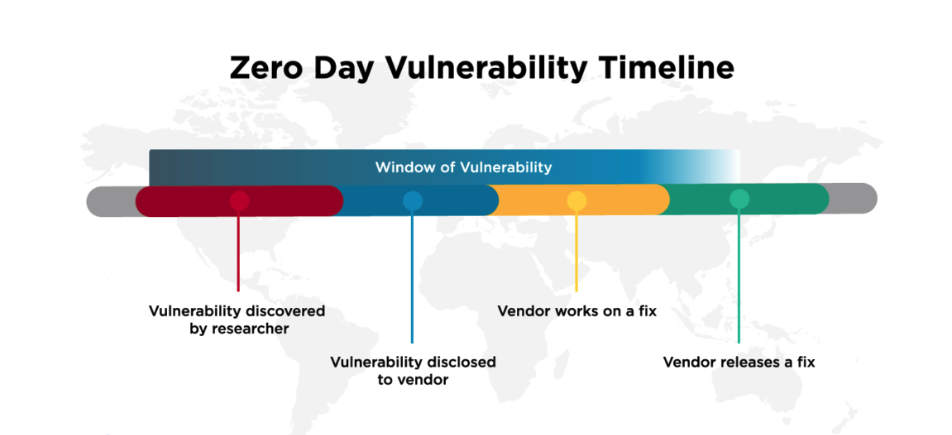
A zero-day vulnerability is a newly acquired software security flaw that has not been patched, because it remains unknown to the software developers. Developers learn of the existence of a zero-day vulnerability only after such an attack occurs: they have had “zero days” notice to patch the vulnerability before the attack occurs.
Security is an aspect that has always been linked to IT and that IT administrators have to deal with on a daily basis. Although the quality level of today’s software is generally very high, over time there are always some vulnerabilities that can be used by third parties with malicious intent. During this time, cybercriminals exploit these undetected vulnerabilities to gain access to systems, steal data or cause other damage. It is important to implement security systems to prevent or minimise these types of attacks, so getting cybersecurity advice and implementing the right protection tools should be a priority for all companies.
How does a zero-day attack work?
A zero-day attack occurs when attackers discover a vulnerability in a computer system before system administrators do and can use it to carry out various types of attacks to steal information, disrupt the system and other malicious practices.
In the software development process, many of the necessary tests are carried out to ensure that programs reach the market without bugs, errors and vulnerabilities. However, it is not until the software runs in a real environment and is used by a large number of users or companies that some vulnerabilities are discovered that pose a real security threat. If cybercriminals discover these problems before a system’s developers or administrators do, they can use them for criminal purposes.
Hackers are facilitated in their ability to attack and infiltrate a company’s systems by potential vulnerabilities in software, both in the operating system and in other software used. If they find a particular vulnerability, they can exploit it to carry out all kinds of attacks against the system. A zero-day attack means that the company is under attack because of a flaw in its systems and that, if it does not react quickly and appropriately, the consequences can be very negative, both from an operational, financial and reputational point of view.
Protections against zero-day attacks
The best way to ensure a fast and effective response is to have a defined protocol for dealing with zero-day attacks. Knowing what to do and when to do it is essential to act in time and minimise the repercussions in case of a zero-day attack.
Since the consequences of such attacks are very serious, it is necessary to implement methods to detect them and tools and policies to combat them should they occur. Zero-day attacks are a big threat because there is no “cure” until a patch is released, and this can take a while. You could be using software that might not be patched for weeks or even months. And many people are slow to update their software even after a patch is released.
During this time, attackers are relentless and try to attack as many users as possible before the patch is released. This can put your data at even greater risk than normal. Some of the solutions we implement in the field of cybersecurity are penetration testing, or pentesting, which consists of attacking a computer system with the intention of finding security weaknesses and anything that could have access to it, its functionality and its data. In this line, a good solution is to carry out Ethical Hacking. Where professionals put themselves in the shoes of potential attackers to identify vulnerabilities in an organisation’s network system. Once identified, they can be fixed before they are discovered by the real cybercriminals. In addition to penetration testing and network security assessment, it is always essential to have a Disaster Recovery and Backup Plan in place to ensure business continuity despite a breach.

