Cybersecurity monitoring with SIEM
Companies are increasingly exposed to cyber threats. Everyone says so, and now the Information Systems Audit and Control Association (ISACA) confirms it in its latest study, recognizing that more than 50% of companies around the world have increased their organization’s risk levels in the last year. As a result, more and more companies are opting for a Security Operations Center (SOC) to prevent, monitor and control network and Internet security.
Security Operations Center (SOC)
A SOC is a specific unit in charge of IT security prevention, monitoring and control. The services it provides range from vulnerability diagnosis to disaster recovery, incident response, attack neutralization, prevention programs, risk management and computer anti-virus alerts.
Equipped with servers, firewalls, intrusion detection systems, antivirus software and other specialized systems, a SOC monitors network and Internet activity in real time, 24 hours a day, 7 days a week. Data events are analyzed and tracked by certified security standards experts. At Cloud Levante, one of the main tools used by our team to perform this comprehensive monitoring is SIEM.
SIEM: the heart of SOC
SIEM refers to two concepts, Security Event Management (SEM) and Security Information Management (SIM).
The first concept, SEM, refers to the monitoring and correlation of events in real time and the second, SIM, to the storage of the data obtained, its analysis and the generation of reports based on the results obtained.
In this sense, SIEM offers a global vision of the company’s IT security and its main function is to detect anomalous behavior in order to prevent the organization from IT threats.
Configuring SIEM
To configure our SIEM, we first install an agent on the machines we want to automate. This agent is responsible for collecting information from the system, protecting it with an EDR or integrating it with the Antivirus already in use, and sending all the information to the SIEM for subsequent analysis and response.
Our configuration allows us to obtain the necessary information, providing a complete visualization of the network points. This will allow us to react in real time to any incident, but also to apply improvement measures when we perceive that the performance of a certain service is not as expected. Some of the data that can be obtained with the SIEM configuration are:
- Analysis of host security events.
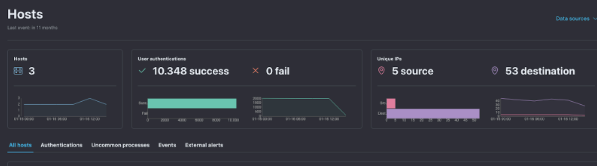
- Analysis of network security events.
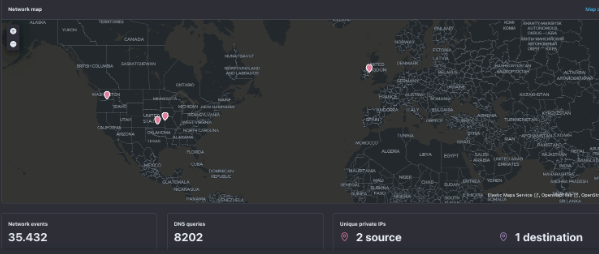
- Reputation and analysis of IP addresses with which communications are established.
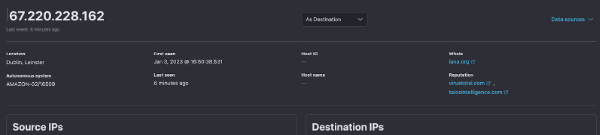
- Timeline event viewer.
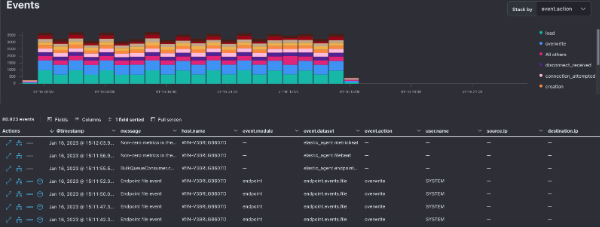
- Detailed and in-depth analysis of the events.
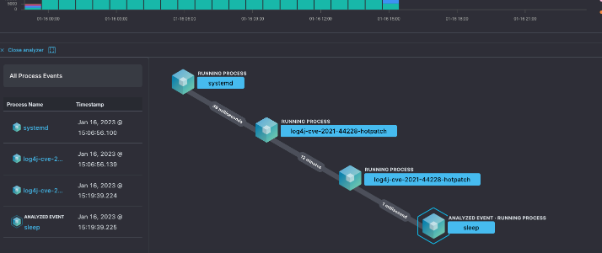
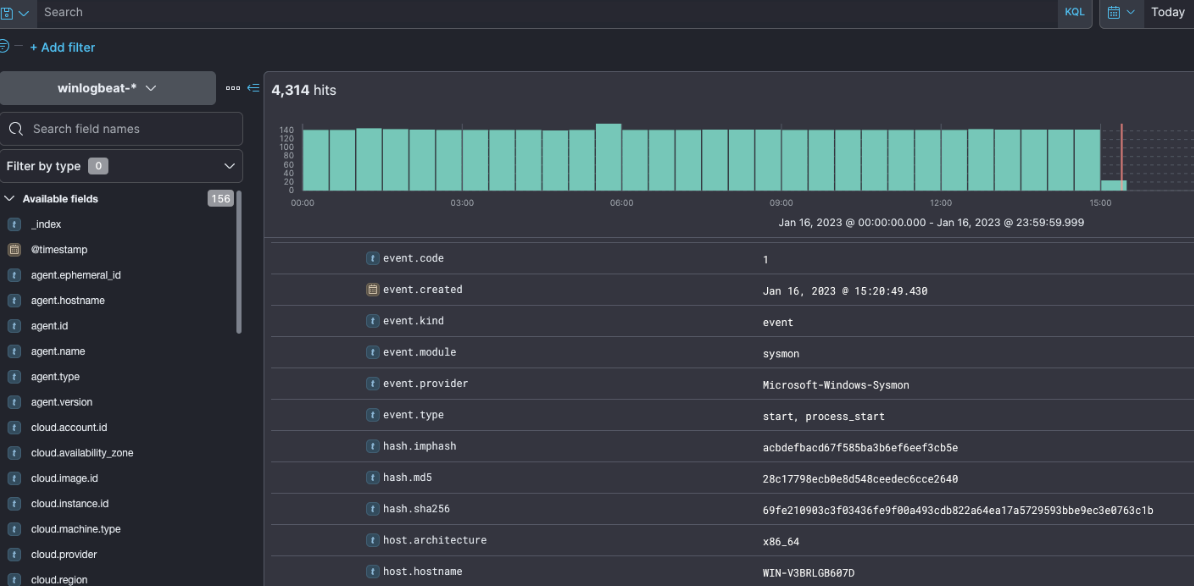
- You can query large volumes of data to establish correlations between certain parameters and perform a deeper search.
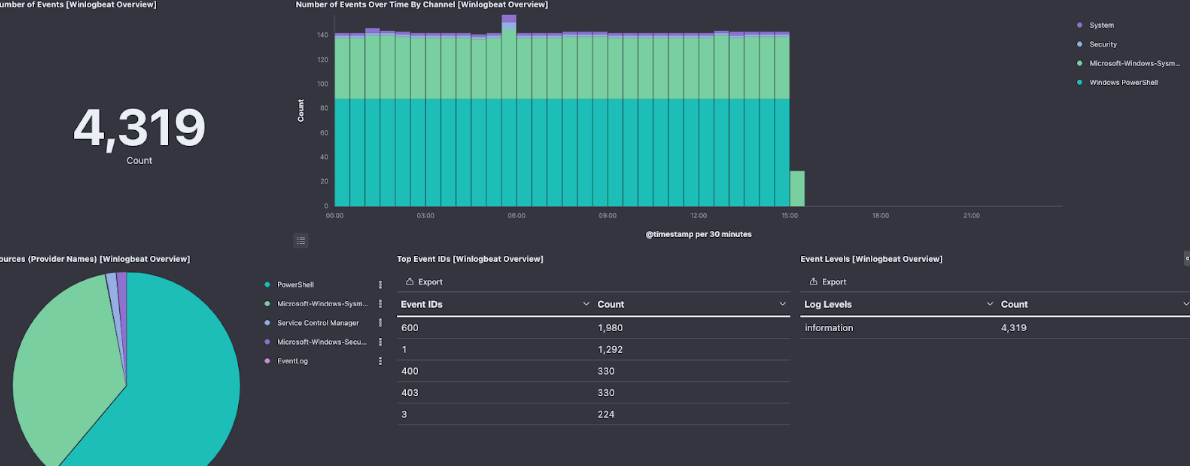
- Dashboards for better data visualization and metrics collection.
High flexibility to collect information from different types of software, services, operating systems or cloud platforms.
- Host Intrusion Detection System (IDS) integration in Elasticsearch
System for monitoring and detecting suspicious activity. It sends us an alert when it is detected so that we can investigate the problem and take appropriate action to remedy the threat.
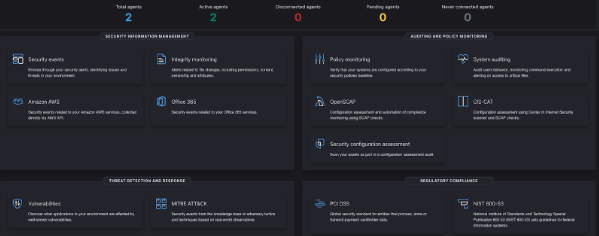
- Various dashboards for the visualization of agents running the IDS.
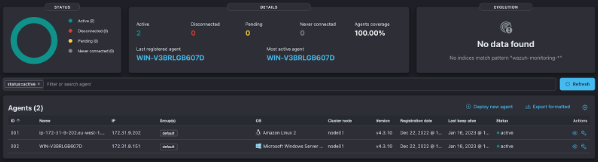
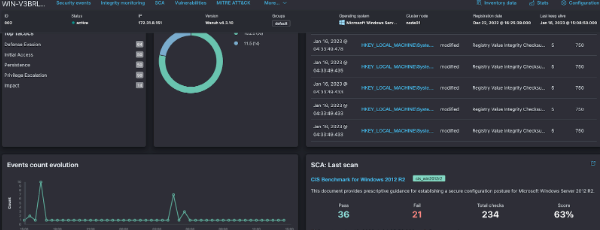
- Vulnerability scans.
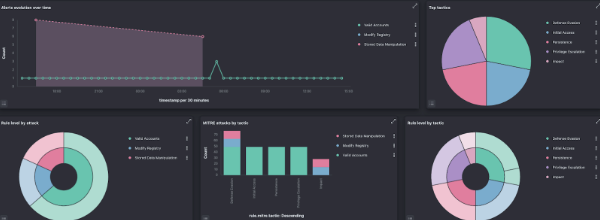
- Mitre ATT&CK framework
Cloud Levante has technicians specialized in cybersecurity, using as a SIEM tool. But adapting the functionalities to each project to offer Adhoc solutions.
Our technical team is always ready to help companies to start the digital transformation process and protect the most critical business data.
If you need advice in this or any other area, please contact us.

