Status of cyber-attacks and how to be resilient in 2023
Cyber-attacks have continued to evolve and increase in frequency and sophistication in recent years, and it is likely that this trend will continue in 2023. Threat actors are constantly finding new ways to exploit vulnerabilities in digital systems, and organizations must remain vigilant in their efforts to protect against these attacks.
Obstacles for companies to undertake a formal review of risks
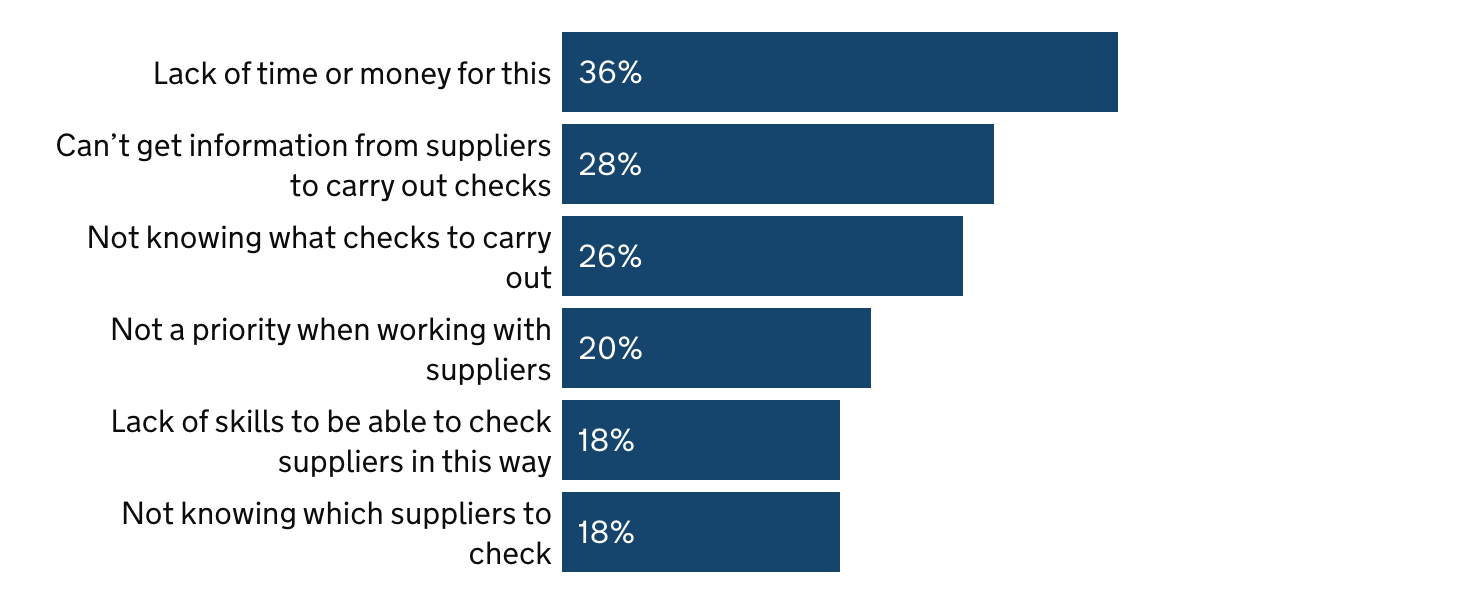
GOV.UK – Official Statistics: Cyber Security Breaches Survey 2022
To give some context, some recent examples of cyber-attacks include:
- During the past year there was a $618 million theft from Axie Infinity.
- Executives and internal staff from different organizations were bribed by the Lapsus$ extortion group, which stole high-profile data to force payment from its victims. Victims included Microsoft, Samsung, Nvidia, Ubisoft, Okta and Vodafone.
- A ransomware linked to RaaS REvil attacked Medibank, gaining access to the personal data of the company’s four million customers. The cost of the vulnerability reached $35 million.
In terms of specific types of attacks, ransomware attacks are likely to remain a significant threat, as they continue to be a lucrative and effective way for attackers to monetize their efforts. Phishing attacks will also remain a common threat. In this regard, we can establish the five most common cyberattacks:
Ransomware: A type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key.
Phishing: A social engineering attack that aims to trick individuals into revealing sensitive information, such as login credentials or financial information, by posing as a trusted entity.
Malware: Short for malicious software, malware refers to any software designed to cause harm to a computer or network.
Zero-day exploit: A security vulnerability that is unknown to the software vendor or the general public, and is being actively exploited by attackers before a patch is released.
Password attack: An attack that aims to compromise a user’s password, often through methods such as brute force attacks, dictionary attacks, or password reuse attacks.
Percentage that report the following types of breaches or attacks as the most disruptive
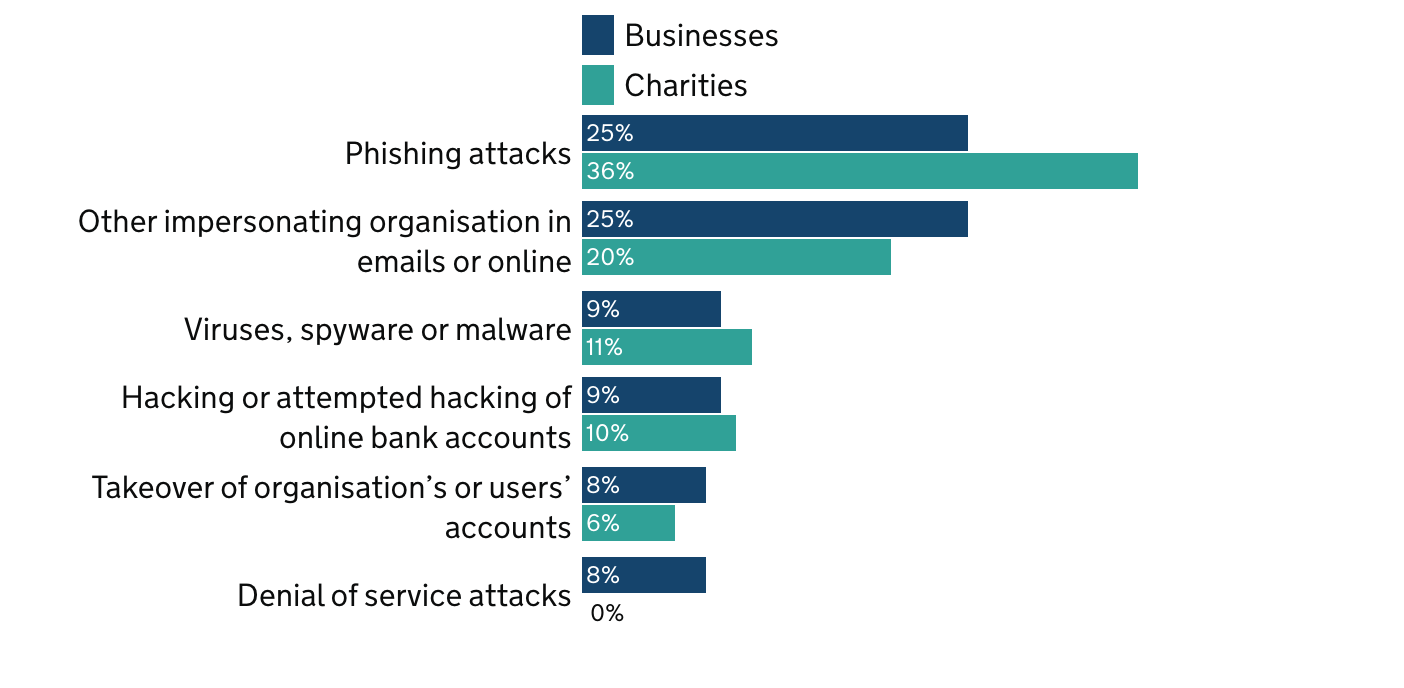
GOV.UK – Official Statistics: Cyber Security Breaches Survey 2022
To avoid it: integral approach to security supported by:
To prevent attacks, we apply a comprehensive approach to security backed by measures such as:
Security by isolation: keeping personal data and Internet activities strictly separated from our anonymous online profiles.
Web browsing in an isolated environment: when visiting untrusted websites, use an isolated virtual machine environment that does not store changes, so that potential browser vulnerabilities do not persist the next time we use the computer, or in different contexts.
Secure VPN: to avoid hacked Wi-Fi networks.
In addition, special considerations must be taken into account for each threat machine:
Ransomware: Regularly backup your critical data, keep your software and systems up-to-date, and do not open suspicious emails or attachments.
Phishing: Be cautious of emails or messages that ask for sensitive information, especially if they come from an unexpected source. Verify the authenticity of the sender before responding.
Malware: Keep your software and systems up-to-date, use anti-virus software and keep it updated, and avoid downloading or installing software from untrusted sources.
Zero-day exploits: Keep your software and systems up-to-date, and implement network and endpoint security controls, such as firewalls and intrusion detection systems.
Password attacks: Use strong, unique passwords and enable two-factor authentication when possible. Avoid reusing passwords across different accounts, and consider using a password manager to securely store your passwords.
It is important to note that no single measure can provide 100% protection against cyber-attacks, and that organizations must adopt a multilayered approach to security in order to increase their resilience against these threats. Security is important to us, if you would like more information please do not hesitate to contact Cloud Levante’s security management team.

