Honeypot to monitor and prevent cyber-attacks
Corporate security is essential. For this reason, our security specialists install Honeypots capable of detecting the number of attacks and their origin. In this way, the necessary measures can be taken so that the current system is not affected by these attacks.
Today in Cloud Levante we are going to talk in detail about the actual implementation of a Honeypot, a fundamental tool to keep your network secure.
A honeypot, or trap system, is a computer security tool installed on a network or computer system to make it the objective of a possible cyber-attack.
The main characteristic of this type of programs is that they are designed not only to protect against a possible attack, but also to serve as an invisible decoy for the attacker. The aim is to detect the attack and obtain information before it affects critical systems.
Honeypot Implementation
The implemented honeypot is a simulation of an infrastructure with different servers and services that exposes all the traffic to the outside to monitor the number of attacks or traffic that can arrive. Depending on the intention of the honeypot, services are selected or all are exposed to collect information.
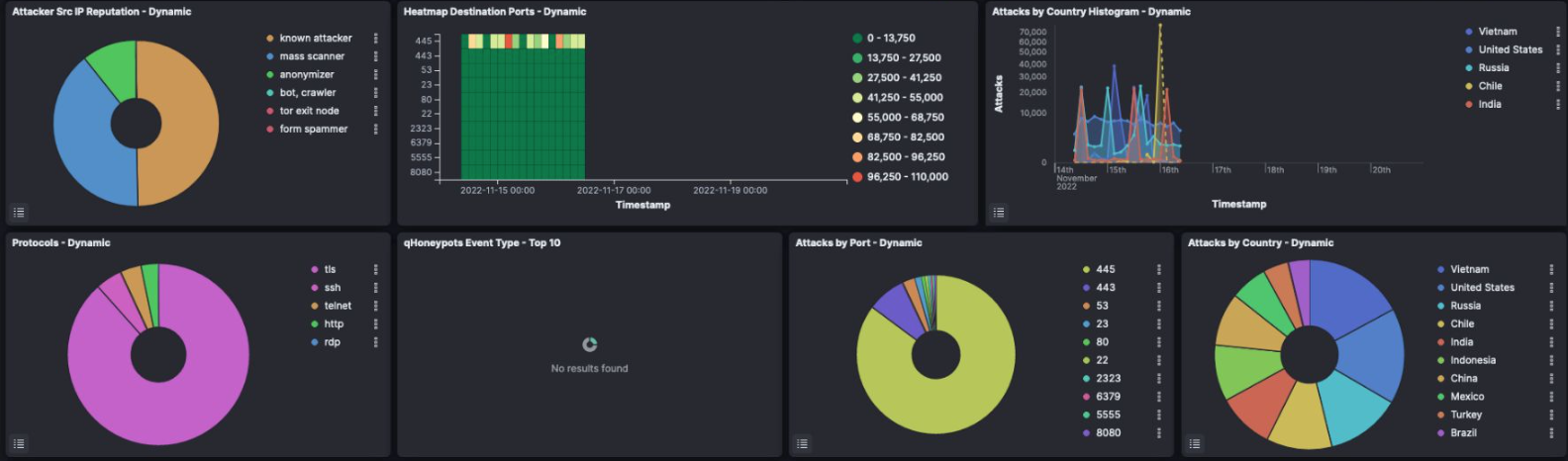
This honeypot has been active for 2 days and has collected 1,101,048 attacks from 5,393 IPs.
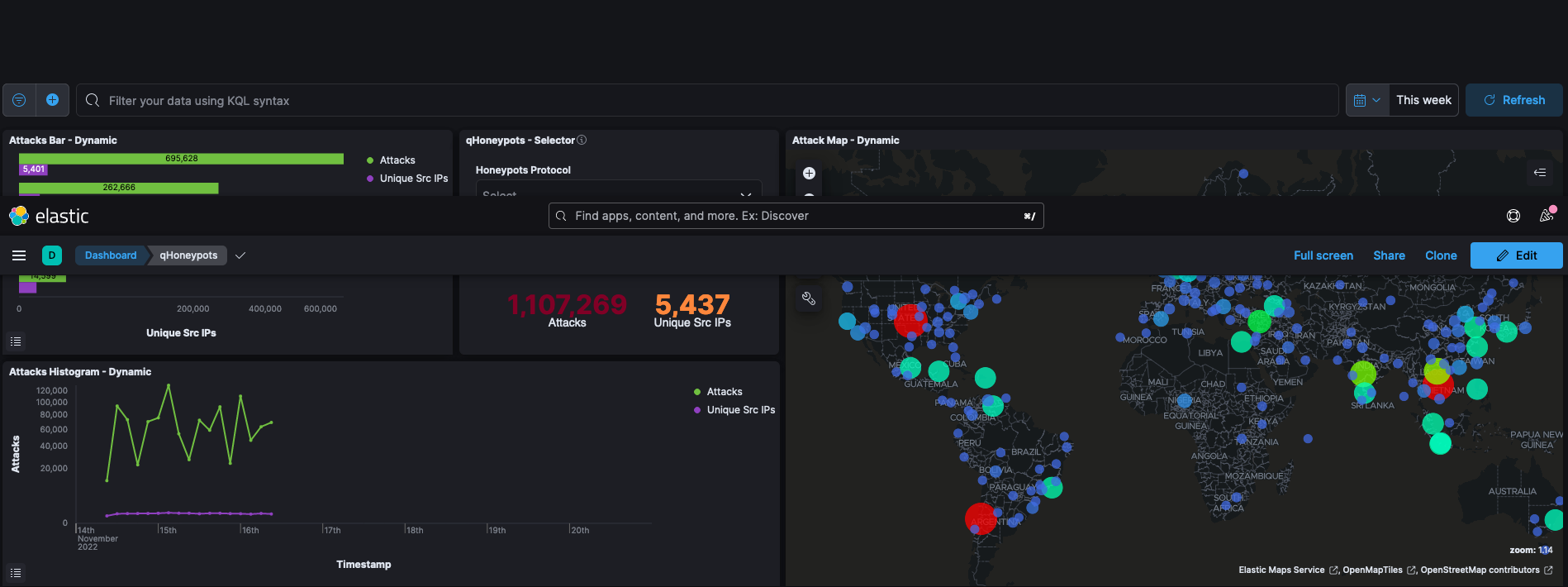
The heat map allows us to know the origin of the attacks, how the number of attacks progresses over time, the targeted ports, the users and passwords to which access has been attempted, etc. An interesting data from the heat map is the number of attacks and their origin. This is useful for us, both to raise awareness and to promote cyber defense with a Security Operations Center (SOC). This platform allows us to monitor and manage the security of information systems through collection tools, event correlation and remote intervention.
In this image we can see the central point, which is where the server is located and the attacks classified by geolocation.

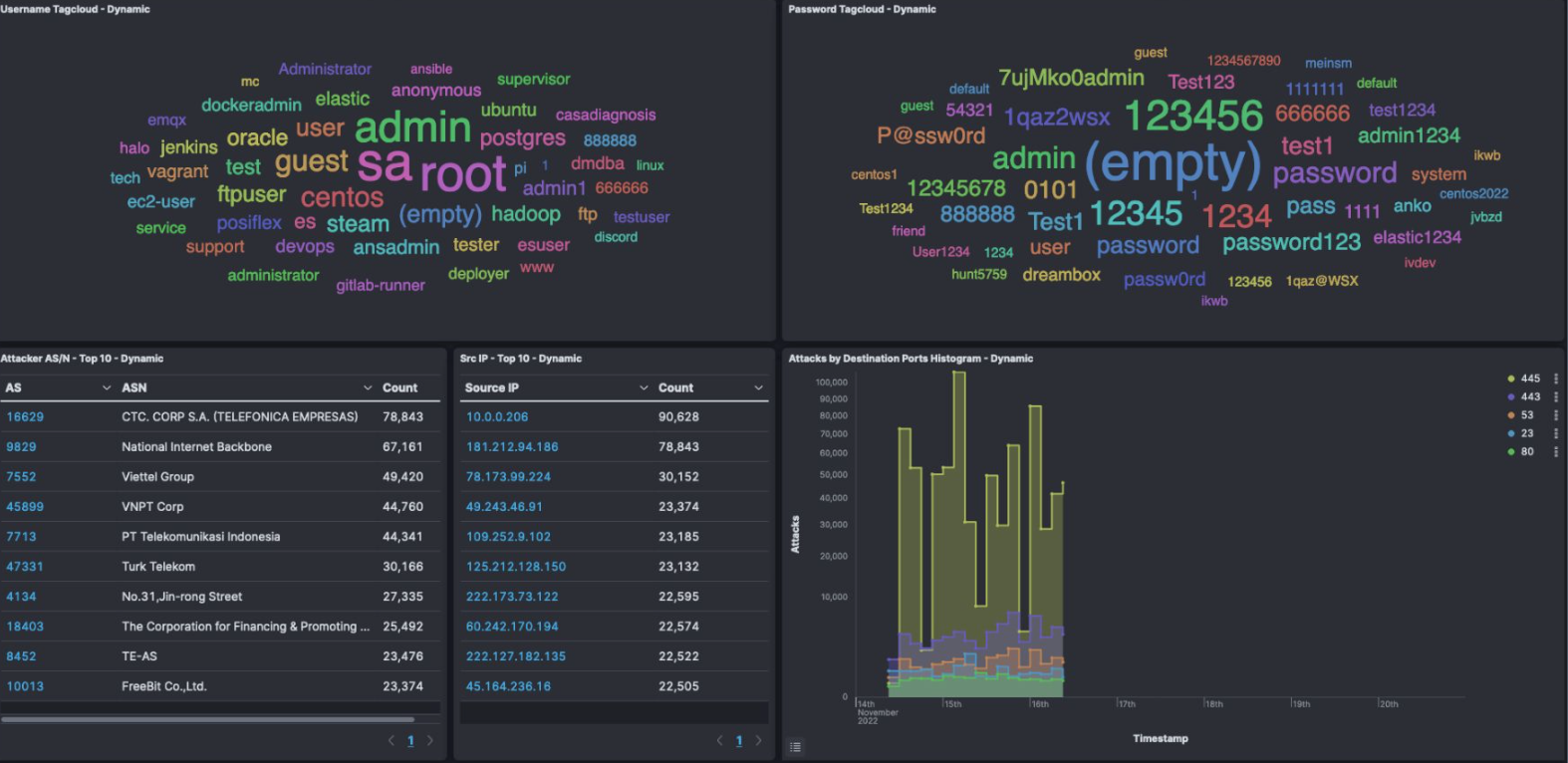
The honeypot allows to know the users, passwords and IP addresses that have tried to access our information. This information is vital to keep an infrastructure up to date against cyber-attacks.
In general, most of these attacks are not detected by antivirus programs, and most of the IPs analyzed are not reflected in the reputation lists. This happens because many are very recent, and the companies that distribute these protection software have not received and catalogued the addresses.
Therefore, a Honeypot identifies all users, passwords and IP addresses.
The honeypot has proven to be a great security mechanism. The variety of data collected reinforces the security policies of any company.
In conclusion, virtual honeypots, which can be installed and configured, are a first-class means of gaining in-depth network knowledge in a real-world, but low-risk environment. For all these reasons, considering the effectiveness of the tools, the honeypot is expanding in the world of cybersecurity, using it to capture hacker activity on the Internet.
